In Part 1, Part 2, and Part 3, I covered the legal basis, backup strategy, policy implementation, locking the recovery points stored in the vault, and applying vault policy to prevent specific actions.
In this part, I will dive deeply into two essential compliance-related topics: Legal Holds and Audit Manager.
Legal Holds
AWS Backup Legal Holds are designed to help comply with legal and regulatory requirements by preventing the deletion of recovery points that may be needed for legal purposes, such as audits, investigations, or litigation. Legal holds are the assurance that critical recovery points are retained and protected from being accidentally or intentionally deleted or altered. At first, this feature might sound similar to the Vault Lock feature, which also prevents deletion of the recovery points if the Vault is in compliance mode. The differences are:
- Legal Holds can be modified or removed by a user with the proper privilege
- Legal Holds tie the recovery point to a date range despite the lifecycle
- Legal Holds can be applied to both Vaults and resource types categorically
- You are limited to 50 scopes per legal hold
The Legal Holds’ date range might initially seem confusing, considering that the recovery points continue to be added to a specific vault. But the use case for Legal Holds differs!
Legal Holds can be helpful in use cases like the retention of specific resource types or recovery points stored in a particular vault to prevent them from being deleted if they backup was taken within the range. The Legal Holds date range is set in order to avoid the deletion of backups despite the lifecycle if the backup was taken within that range. For example, a data breach occurs, and the bank must investigate and report on the incident. Backups related to the breach are stored in an S3 bucket; the database snapshot and EBS volumes are all stored in the Daily vault and need to be preserved for both internal review and external reporting to regulators for the next two years from the date of the incident. In this scenario, Legal Holds can be used to protect the recovery points related to the investigation.
From the Backup console sidebar menu, navigate to Legal Holds and add a new Legal Hold.
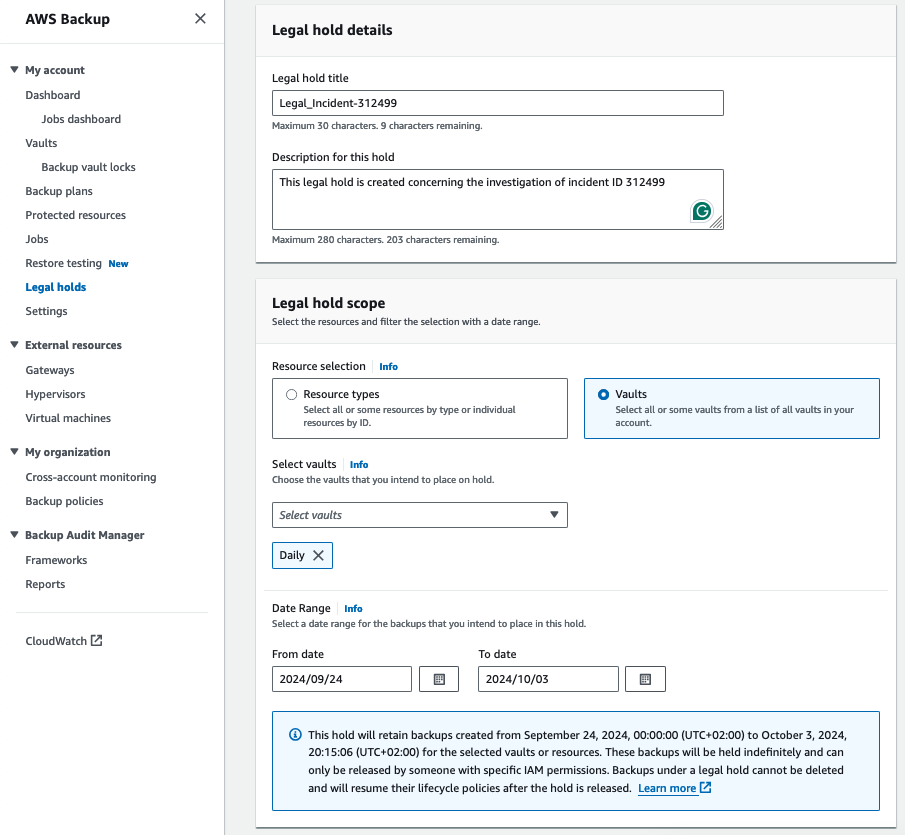
It is also possible to add tags when creating a legal hold to make the protected resources more easily identifiable.
Audit Manager
AWS Backup Audit Manager was announced in 2021, and it is one of the most critical features for legal compliance and reporting on cloud infrastructure backup protection. Without the Audit Manager, a company must implement custom tools and scripts to provide a similar report to auditors and regulators.
Firstly, AWS Config must be enabled for Audit Manager Framework to function. The reason for requiring AWS Config is that the resource changes are tracked via Config, including resources deployed in an account, resources that are a part of a backup plan, etc.
On the home page of Audit Manager Frameworks, you will see pretty good how-to-start steps:
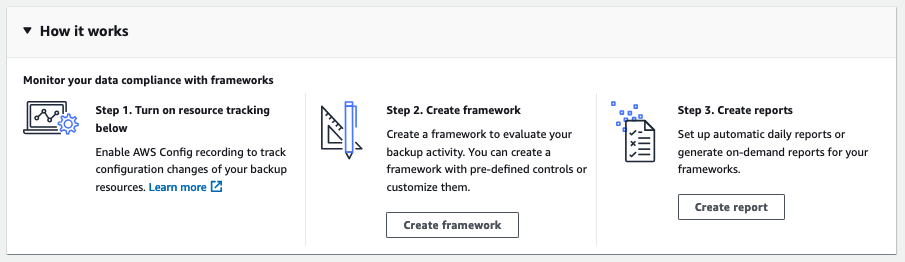
Before creating a framework, let’s look at another feature of Audit Manager called Reports.
Report plans allow you to create recurring and on-demand reports to audit your backup activity, including cross-account and cross-Region reports.
Not all reports require a Framework. Here is how they work:
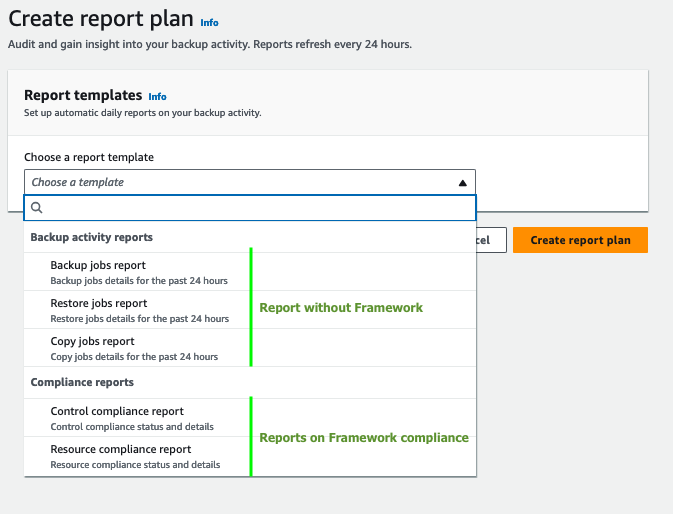
The two Compliance reports will report on the state of resources in conjunction with the pre-defined framework. You can look at the compliance framework as a representation of the organization’s backup policy written in a document.
Let’s create a Framework to understand it better. I set a name for the Framework called PolicyComplianceFramework. There are 11 controls that can be configured:
- Resources are protected by a backup plan
- Backup plan minimum frequency and minimum retention
- Vaults prevent manual deletion of recovery points
- Recovery points are encrypted
- Minimum retention established for recovery point
- Cross-Region backup copy scheduled
- Cross-account backup copy scheduled
- Backups protected by AWS Backup Vault Lock
- Last recovery point created – new
- Restore time for resources meet target – new
- Resources are inside a logically air-gapped vault – new
As you can see, the controls cover a reasonably wide range of evaluations. Each control can be configured independently based on a specific resource type, resource tag, or even a single resource.
I made some changes to the control settings to meet my backup policy compliance report requirements:
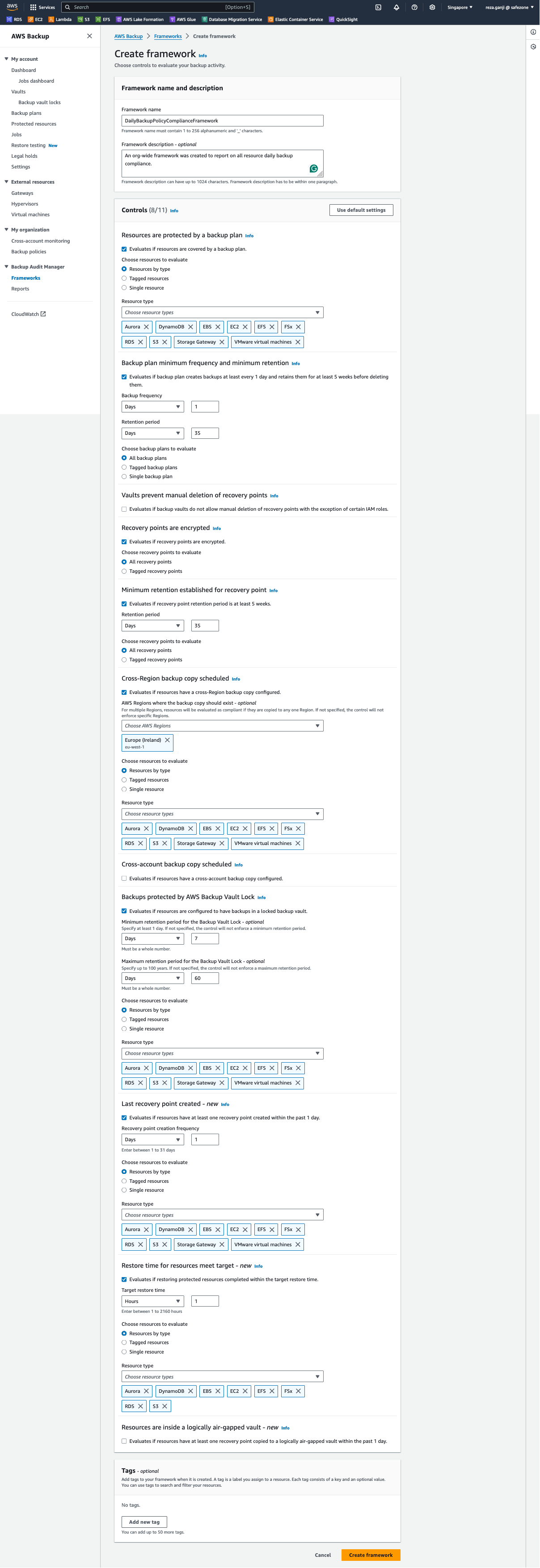
As you can see, I disabled these three controls and why:
- Vaults prevent manual deletion of recovery points.
- Evaluates if backup vaults do not allow manual deletion of recovery points with the exception of certain IAM roles.
- Why disabled? All vaults must have a lock enabled in compliance modes, which does not allow deletion by design.
- Cross-account backup copy scheduled
- Evaluates if resources have a cross-account backup copy configured.
- Why disabled? AWS Backup does not support cross-account AND cross-region copies of the recovery points simultaneously. I am copying the recovery points to another region, and as such, no cross-account copy is possible.
- Resources are inside a logically air-gapped vault – new
- Evaluates if resources have at least one recovery point copied to a logically air-gapped vault within the past 1 day.
- Why disabled? I am not using air-gapped vaults as I prefer to control the recover points cross-region copy and its storage location.
After the framework is created, it will take some time to aggregate and evaluate the resources. As a reminder, frameworks cannot function without AWS Config.
Now that the audit framework is created, I will explain the Backup Report Plans.
In almost every certification, and indeed, DORA included, the auditors will ask for a backup job report. A backup job report is one way to automate the report generation and ease the auditing process. You will need to decide which accounts and OUs are included in the job report and also need to create an S3 bucket to store the automatically generated reports.
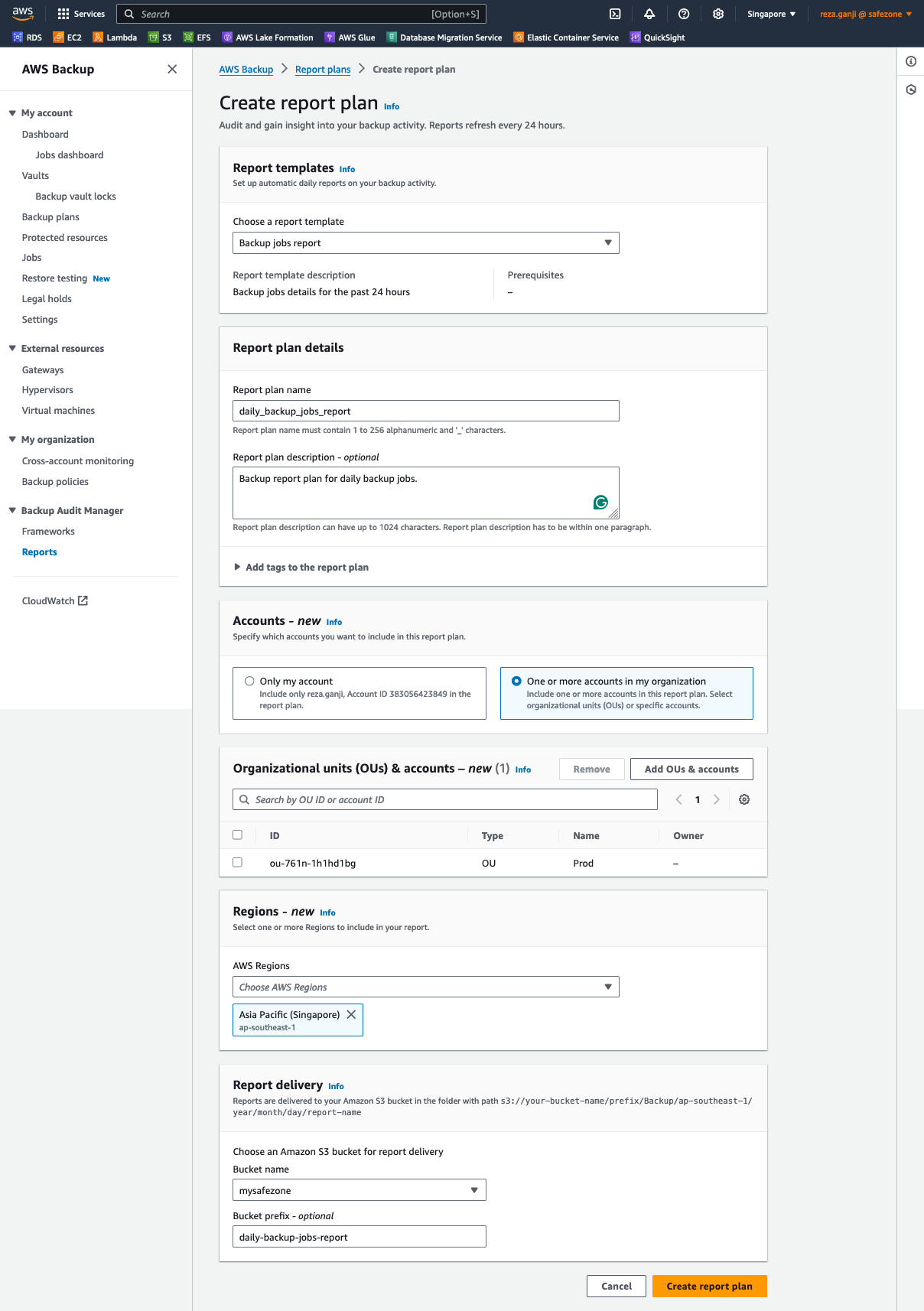
With this report plan created, I can now provide the backup job success/failure report to auditors anytime. Also, I will make one more report that is linked to the framework that was created.
This report will be a compliance report to ensure that the resources are in compliance with all the resources covered in the backup policy. Similarly, you must configure the OUs and accounts in the report and an S3 bucket to store the daily report. The report refreshes every 24 hours.
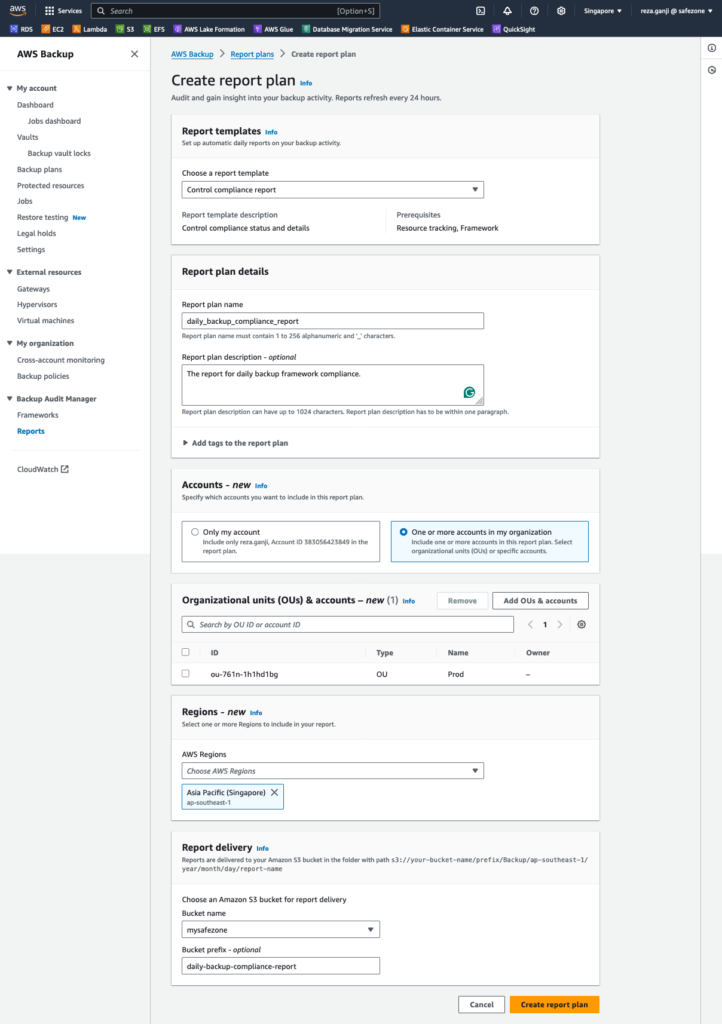
In this part, we reviewed how AWS Backup Audit Manager works and how Legal Holds can be handy in specific use cases. Finally, we generated audit reports based on the created framework and stored the reports in an S3 bucket.
As a reminder, here is what the target architecture diagram looks like:
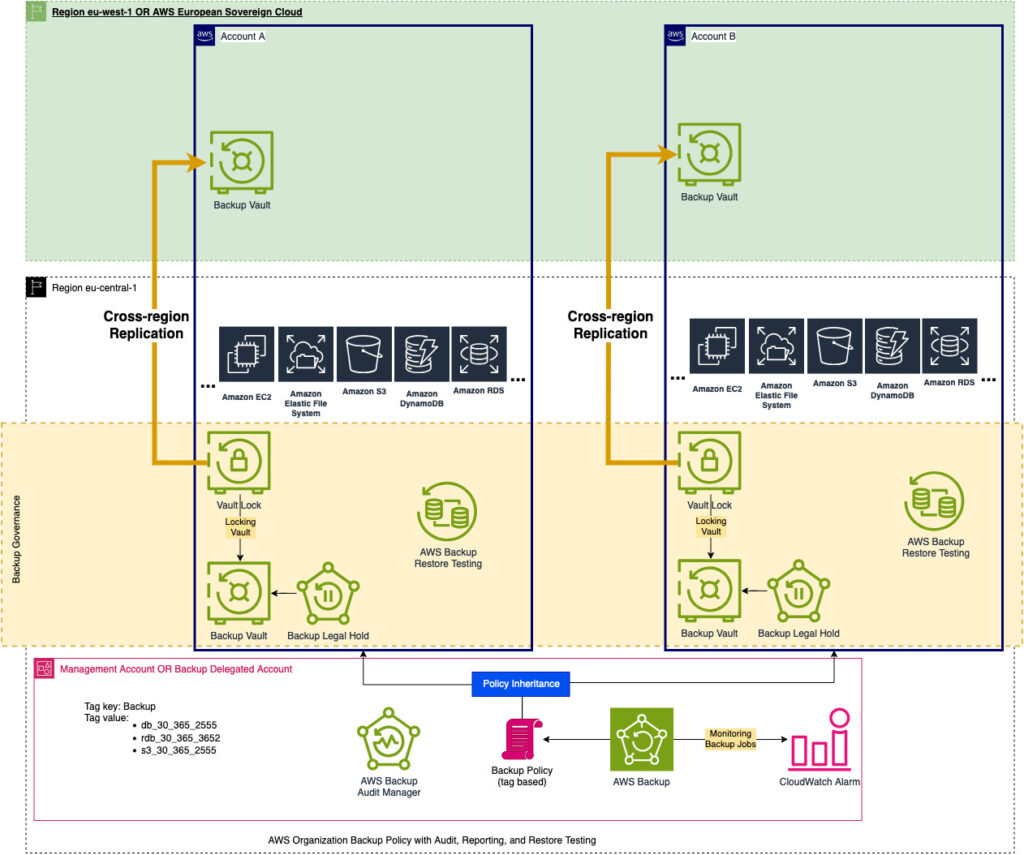
In the next part, I will elaborate on AWS Backup Restore Testing.
End of Part 4 – Stay tuned!

Leave a Reply