- Turning Markdown into GuardrailsA Hands‑On Review of Amazon Q’s Custom Rules for Shift‑Left Governance Spoiler: in less than an hour I transformed two plain‑English Markdown files into 22 actionable findings that Amazon Q surfaced directly in VS Code. Why This Matters Modern engineering teams already live in their IDEs and CI pipelines; meanwhile security, compliance and architecture guidance too often sits in PDFs or wikis that no one reads until audit time. Amazon Q’s new Custom Context Rules feature collapses that gap by letting you drop Markdown rulebooks into a special folder (.amazonq/rules/). The AI assistant then enforces those rules every time you: In other words, your… Read more: Turning Markdown into Guardrails
- Why AWS Bottlerocket is a Must-Have for Containerized WorkloadsContainers have completely transformed how I approach building, deploying, and managing applications. Their lightweight nature and ability to encapsulate dependencies have made them the foundation of my modern development workflows. When I discovered AWS Bottlerocket, a Linux-based operating system (OS) from Amazon Web Services, it felt like the perfect match for optimizing and securing containerized environments. Let me share my experience with what it is, its capabilities, and why I think it’s worth considering. What is AWS Bottlerocket? AWS Bottlerocket is an open-source, minimalist OS tailored specifically for running containers. Being open-source means that Bottlerocket benefits from community-driven contributions, which… Read more: Why AWS Bottlerocket is a Must-Have for Containerized Workloads
- Secure Software Supply Chain with AWS Signer for Secure Code SigningIn today’s digital world, ensuring your software is secure and trustworthy is more important than ever. With supply chain attacks becoming more common, code signing is one effective way to protect your software. In this article, I will walk you through what code signing is, why it’s essential, and how AWS Signer can help you do it at scale—while also keeping up with regulations like the EU’s DORA act. What Is Code Signing? Code signing is a process that ensures your software, like an app or script, hasn’t been changed or tampered with since the original author signed it. Essentially,… Read more: Secure Software Supply Chain with AWS Signer for Secure Code Signing
- Mastering AWS Backups: DORA Compliance with Robust Backup & Restoration Strategies – Part 5 (final)In Part 1, Part 2, Part 3, and Part 4, I covered the legal basis, backup strategy, policy implementation, locking the recovery points stored in the vault, applying vault policy, legal holds, and audit manager to monitor the backup and generate automated reports. In this part, I will explore two essential topics that are also DORA requirements: restore testing and Monitoring and alarming. Restore Testing Restore testing was announced late last year on Nov 27, 2024. It is extremely useful and one component that can ease the operational overhead of backups. …[Restore Testing] helps perform automated and periodic restore tests… Read more: Mastering AWS Backups: DORA Compliance with Robust Backup & Restoration Strategies – Part 5 (final)
- Mastering AWS Backups: DORA Compliance with Robust Backup & Restoration Strategies – Part 4In Part 1, Part 2, and Part 3, I covered the legal basis, backup strategy, policy implementation, locking the recovery points stored in the vault, and applying vault policy to prevent specific actions. In this part, I will dive deeply into two essential compliance-related topics: Legal Holds and Audit Manager. Legal Holds AWS Backup Legal Holds are designed to help comply with legal and regulatory requirements by preventing the deletion of recovery points that may be needed for legal purposes, such as audits, investigations, or litigation. Legal holds are the assurance that critical recovery points are retained and protected from… Read more: Mastering AWS Backups: DORA Compliance with Robust Backup & Restoration Strategies – Part 4
- Mastering AWS Backups: DORA Compliance with Robust Backup & Restoration Strategies – Part 3In Part 1 and Part 2, I covered the legal basis, backup strategies, and retention and briefly touched on vaults. In this part, I will cover policy creation in the root or backup delegated account, configuring Vaults & its compliance lock, legal holds, and resource selection. Vaults Configuration To begin with, let’s create three standard vaults for all the recovery points: daily, monthly, and yearly. We’ll need to repeat this step for monthly and yearly vaults. Once the vaults are created, we can add specific policies to them. Let’s not forget that one of DORA’s requirements is about who can… Read more: Mastering AWS Backups: DORA Compliance with Robust Backup & Restoration Strategies – Part 3
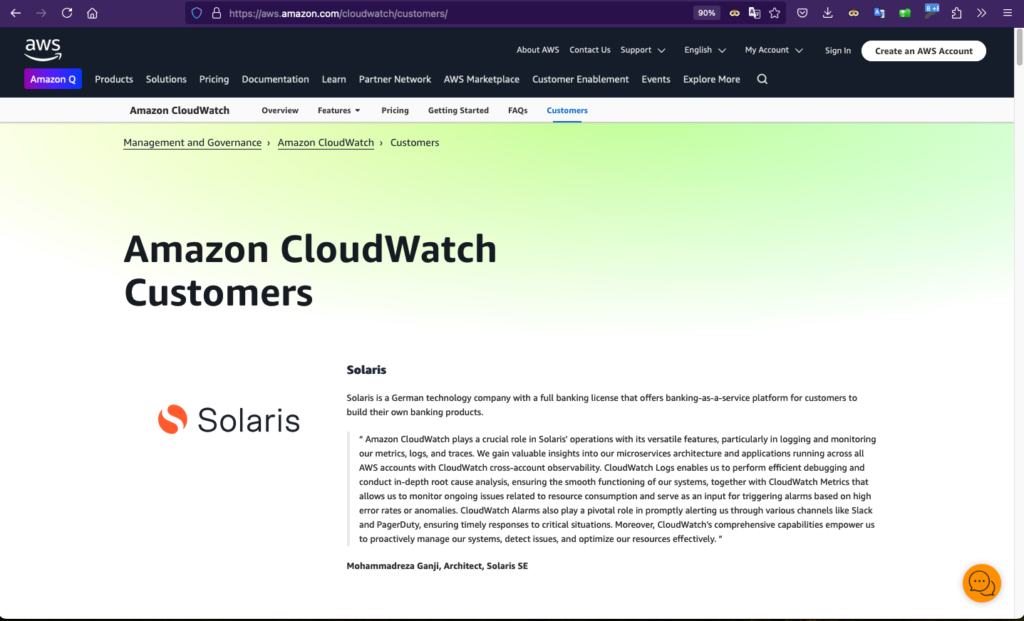
- My CloudWatch testimonial on AWS websiteI was asked to provide a testimonial for CloudWatch due to the level of usage and the way it was architected and used in the organization, and here is where you can see my words: https://aws.amazon.com/cloudwatch/customers Screenshot:
- Mastering AWS Backups: DORA Compliance with Robust Backup & Restoration Strategies – Part 2In Part 1, I emphasized DORA’s requirements and the overall architecture of resource backup within an organization. In this part, I will focus on backup initiation strategies, vaults, retention of the recovery points, and tagging policy. Backup Strategies If the resources in your AWS Organization are managed via code, aka infrastructure as code, you are on good terms. Otherwise, you will need to spend some time categorizing and structuring your resources based on their type and data retention. First, let’s define the retention of the resources and its data based on the legal requirements. For example, as a financial entity,… Read more: Mastering AWS Backups: DORA Compliance with Robust Backup & Restoration Strategies – Part 2
- Mastering AWS Backups: DORA Compliance with Robust Backup & Restoration Strategies – Part 1When discussing cloud resource backup and restoration, there are many ways to handle them. You may wonder what the best way is! Should you use backup and restoration software that you might be already familiar with from your on-premises data center, like Vaeem? Or should you consider using software built in the age of cloud-native solutions? You will find the answers to those questions in this post. I tried to simplify the selection process based on organizational needs. If you must comply with DORA, this is the right stop for you. If you do not have to comply with DORA… Read more: Mastering AWS Backups: DORA Compliance with Robust Backup & Restoration Strategies – Part 1
- Mastering DevSecOps: Leveraging Expertise for Large-Scale SolutionsDeveloping and Implementing Large-Scale DevSecOps Solutions The development and implementation of large-scale DevSecOps solutions is a multifaceted process that demands a comprehensive approach. Integrating security into every phase of the development and operations lifecycle is paramount. This integration ensures that security measures are not merely an afterthought but a fundamental component of the entire process. Leveraging both business and technical acumen is crucial to address complex issues effectively and generate innovative solutions. A key methodology in developing robust DevSecOps solutions involves the adoption of a shift-left security approach. By embedding security practices early in the development process, potential vulnerabilities can… Read more: Mastering DevSecOps: Leveraging Expertise for Large-Scale Solutions
- Harnessing Expertise in DevSecOps: A Strategic Approach to Complex SolutionsLeveraging Business and Technical Acumen for Large-Scale DevSecOps Solutions In the realm of large-scale DevSecOps solutions, a profound understanding of both business and technical facets is paramount. This dual expertise is not merely beneficial but essential for developing and implementing solutions that are both robust and scalable. A comprehensive approach that synthesizes business objectives with technical capabilities ensures that the solutions not only address immediate security concerns but also align seamlessly with long-term organizational goals. For instance, consider the deployment of a large-scale DevSecOps framework within a multinational corporation. The technical team might focus on integrating advanced security protocols and… Read more: Harnessing Expertise in DevSecOps: A Strategic Approach to Complex Solutions
- Mastering Large-Scale DevSecOps Solutions: A Strategic ApproachDeveloping and Implementing Large-Scale DevSecOps Solutions Developing and implementing large-scale DevSecOps solutions requires a meticulous approach, emphasizing the integration of security practices within the DevOps framework to ensure a robust and secure software development lifecycle. The cornerstone of this integration lies in embedding security directly into the continuous integration and continuous deployment (CI/CD) pipelines, ensuring that security is not an afterthought but a fundamental component of the development process. One of the pivotal methodologies in DevSecOps is Infrastructure as Code (IaC), which allows for the automated management and provisioning of technology infrastructure through machine-readable configuration files. By treating infrastructure the… Read more: Mastering Large-Scale DevSecOps Solutions: A Strategic Approach
- Leveraging DevSecOps Expertise to Drive Business SuccessChampioning Strategic Initiatives in DevSecOps Expertise in DevSecOps is instrumental in spearheading strategic initiatives that align technical solutions with overarching business objectives. By leveraging a deep understanding of DevSecOps principles, one can effectively identify and implement strategies that drive impactful results. The alignment of DevSecOps with business goals ensures that technological advancements contribute directly to the company’s success, optimizing both operational efficiency and innovation capacity. One of the critical aspects of championing DevSecOps initiatives is the ability to foresee and address complex technical challenges. For instance, in a recent project, we encountered substantial security vulnerabilities during the integration phase of… Read more: Leveraging DevSecOps Expertise to Drive Business Success
- Driving Success Through Expertise in Large-Scale DevSecOps SolutionsLeveraging Technical and Business Acumen for Effective DevSecOps Solutions Developing and implementing large-scale DevSecOps solutions requires a blend of both technical expertise and business acumen. By integrating security into the development process, I ensure that applications are not only robust but also secure. My approach involves utilizing a variety of methodologies and tools to embed security measures from the outset, mitigating risks and enhancing the overall quality of the software. One methodology I employ is the Continuous Integration/Continuous Deployment (CI/CD) pipeline, which automates the integration and deployment of code changes. By integrating security checks at each stage of the pipeline,… Read more: Driving Success Through Expertise in Large-Scale DevSecOps Solutions
- Driving Success with Large-Scale DevSecOps Solutions: A Techie’s JourneyMastering DevSecOps: Leveraging Business and Technical Acumen Developing and implementing large-scale DevSecOps solutions demands a harmonious blend of business acumen and technical expertise. The primary goal is to integrate security seamlessly into the DevOps process, ensuring that security considerations are embedded throughout the development lifecycle. This holistic approach to security mitigates potential vulnerabilities early in the development phase, reducing risks and enhancing the overall resilience of the software. One of the critical aspects of successful DevSecOps implementation is the ability to combine business knowledge with technical skills. This dual approach enables the identification of complex issues and the generation of… Read more: Driving Success with Large-Scale DevSecOps Solutions: A Techie’s Journey
- Presented at Financial Services Industry (FSI) Forum Berlin hosted by AWSSatyajit Ranjeev and I had the pleasure of attending the Amazon Web Services (AWS) FSI Forum in Berlin. The AWS FSI Forum is dedicated to inspiring and connecting the Financial Services community in Germany, Austria and Switzerland. M. Reza and Satyajit took to the stage to share their insights from Solaris’ migration journey to AWS, highlighting how it has fundamentally transformed our infrastructure and service security from the ground up, improving our foundational technologies and fostering an architectural evolution. “Our deeper engagement with AWS technologies has enabled us to develop solutions that benefit our partners and customers alike. An added… Read more: Presented at Financial Services Industry (FSI) Forum Berlin hosted by AWS
- Configuring AWS Control Tower with AWS SSO and Azure ADLimitations: AWS SSO Limitations: Azure Active Directory (AAD) Limitations: Control Tower Limitations: Miscellaneous Limitations: Considerations: When configuring AWS Control Tower with AWS SSO and Azure Active Directory (AAD), there are several considerations to keep in mind: Configuration: To configure AWS Control Tower with AWS Single Sign-On (SSO) and Azure Active Directory (AAD), you need to follow these steps:
- Impacts of Intellectual Dishonesty at WorkplaceIntellectual dishonesty at the workplace can have significant impacts on individuals, teams, and the overall work environment. Here are some potential impacts: To maintain a healthy work environment, it is essential for individuals and organizations to promote intellectual honesty, transparency, and integrity. By encouraging open communication, fostering a culture of honesty, and implementing policies that discourage dishonest behavior, organizations can mitigate the negative impacts of intellectual dishonesty and promote a positive and ethical workplace. How to avoid intellectual dishonesty at the personal level? Avoiding intellectual dishonesty requires self-awareness, personal integrity, and a commitment to ethical behavior. Here are some ways… Read more: Impacts of Intellectual Dishonesty at Workplace
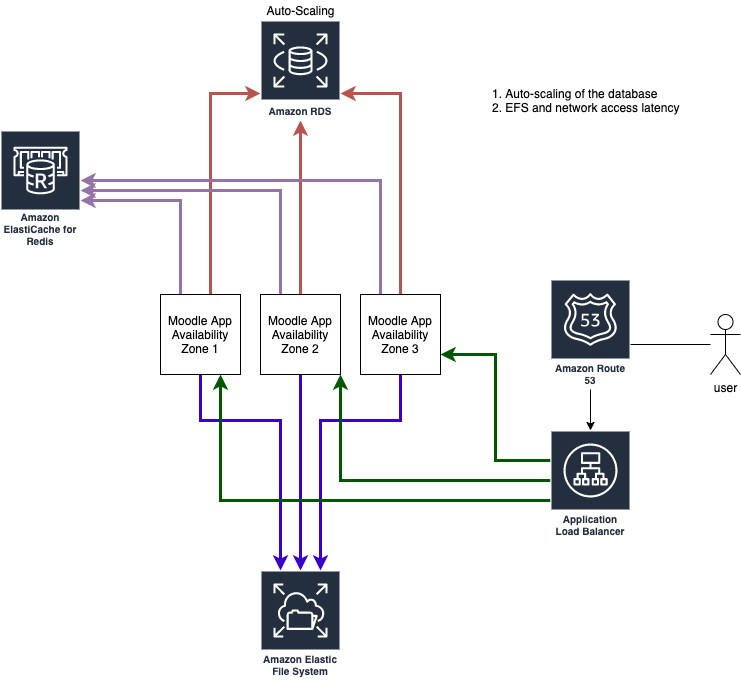
- This is how we hit the limit in Amazon EFSWhen we architect the application, it is essential to consider the current metrics and monitoring logs to ensure its design is future-proof. But sometimes, we do not have the necessary logs to make the right decisions. In that case, we will let the application run in an architecture that we think seems optimized – using the metrics we had access to – and let it run for a while to capture logs required to apply necessary changes. In our case, the application has grown to the point where we could not expect it to happen! The COVID-19 has increased the… Read more: This is how we hit the limit in Amazon EFS
- Communication and failure in information flowCommunication is the activity or process of expressing ideas and feelings or of giving people information; “an apparent answer to the painful divisions between self and other, private and public, and inner thought and outer word.”. According to the Oxford dictionary, communication means “the activity or process of expressing ideas and feelings or giving people information” (Peters, 1999). However, in reality, communication is not just about the transmission of information amongst people. It starts with the willingness to initiate this transmission of info. if the transmitter of information does not believe that the information will be actred upon or that… Read more: Communication and failure in information flow
- How to use EFS to store cx_Oracle, Pandas, and other python packages?This post focuses on how to use the EFS storage to store large packages and libraries like cx_Oracle, pandas, and pymssql and import the packages in AWS Lambda. Considering the Lambda package size limitation that is inclusive of layers, larger functions packages and libraries must be stored outside the Lambda package. There are some steps that you do not need to follow as it has been done, and you can mount the EFS to your lambda and import the package. However, I will be logging the steps to ensure we all can reference the steps in the future – technical… Read more: How to use EFS to store cx_Oracle, Pandas, and other python packages?
- AWS Education Executive ForumThe AWS Education Executive Forum on 2nd June, a live session from 9.30-11.30 am, is an intimate session for 10-15 executive customers from the education sector in Malaysia to share and discuss the digital transformation journey and how cloud innovation can help to achieve the journey. This executive forum is a part of the AWS Initiate ASEAN Online on 10th June, which is a global marketing event series built for customers newest to the cloud, with the overarching theme – Innovation Everywhere. This online event is designed to connect and raise awareness of the value of cloud adoption and help… Read more: AWS Education Executive Forum
- Top reviewer on Gartner Peer Insights!I received a badge from Gartner Peer Insights on productivity solutions: I’m gonna send more reviews on security and cloud soon.
- EDuTECH Asia 2021 – Digital transformation for higher-educationOn 25th Feb 2021 I joined the executive panel discussion that was hosted by AWS on the topic Digital Transformation in Education and Adapting to the New Normal. EduTECH Malaysia 2021 is set to take place on 24-25 February virtually. Over the course of two days, there will be over 60 presentations and live panel debates from leading educators and ed-tech innovators in Malaysia. There will be interaction, Q & A, and live town hall sessions. It will bring together education leaders, policymakers, decision-makers, professionals, technology partners, and stakeholders across the region to inspire, learn, collaborate and innovate. I shared… Read more: EDuTECH Asia 2021 – Digital transformation for higher-education
- Managing HumansA while ago, one of my colleagues suggested reading the book with the title “Managing Humans: Biting and Humorous Tales of a Software Engineering Manager” by Michael Lopp. I really enjoyed it, and I had to share it with my network. I am so glad that I took the advise and read the book (actually listened). Thanks, Ismail Siraj.
- 3rd Annual Digital Transformation Summit MalaysiaI’ll be presenting Co-botting” with Automation: Raising efficiencies in repetitive tasks with robot-human collaborationAt3rd Annual Digital Transformation Summit, 18th-19th November 2020 #digitaltransformation #automation #innovation #cloud #apistrategy
- Ringelmann EffectRingelmann effect. We need to keep the teams small, and that is why the concept of two pizza teams was born. “We try to create teams that are no larger than can be fed by two pizzas,” said Jeff Bezos. “We call that the two-pizza team rule.” Image source:https://lnkd.in/gBVedy6 #leadership #leadershipdevelopment #teamsize #teamwork #team #devops
- Presentation at International e-Conference on New Normal in Education 2020 (IENNE 2020)The conference was organized by Mindware PLT and Akademi Pengajian Bahasa (APB) UiTM, Shah Alam. IENNE 2020 aims to bring together experts in the field, practitioners, scholars and various stakeholders to share pertinent issues and challenges in emerging ‘new normal’ in COVID-19 environment. It is a great opportunity to discuss new possibilities for sharing insights and to develop sustainable professional networks at an important crossroad towards new normal education. Session 11 “Business, Marketing, Management and Social Innovations” 11:05-13:00 | November 29, 2020 (Sunday) Paper ID Title IENNE-034 Case Study: Organizational growth, the Case of LEGO Presenter: Reza Ganji. IENNE-035 External… Read more: Presentation at International e-Conference on New Normal in Education 2020 (IENNE 2020)
- Microsoft Teams is NOT your next LMSIn the past eight months, there has been an astonishing number of changes in how learners receive content and learning materials, as well as the communication methods with instructors. During this period, the changes were far more than what we had seen in the past four to five years combined. Considering how fast institutions had to apply the changes to survive the pandemic, the usual change processes were either not considered or partially ignored. Like any IT organization, my team and I had to ensure our clients could keep up with the changes, including the necessary pieces of training, infrastructure… Read more: Microsoft Teams is NOT your next LMS
- BureaucracyIt’s usual to assume bureaucracy is a terrible thing. But interestingly it has its own advantages.I was reading about Bureaucracy Theory and came across the advantages of bureaucracy.It increases creativity, predictability, scalability, and discourages favoritism. Interesting read:https://lnkd.in/gWjKErk #management #creativity #leadership #bureaucracy