When discussing cloud resource backup and restoration, there are many ways to handle them. You may wonder what the best way is! Should you use backup and restoration software that you might be already familiar with from your on-premises data center, like Vaeem? Or should you consider using software built in the age of cloud-native solutions?
You will find the answers to those questions in this post. I tried to simplify the selection process based on organizational needs. If you must comply with DORA, this is the right stop for you. If you do not have to comply with DORA and you still want to take control of your backups in a comprehensive manner, then you are doing the right thing, as anything can happen at any time, especially with ever-changing resources running on the cloud.
The Digital Operational Resilience Act (DORA) outlines specific requirements for financial entities regarding the resilience of their ICT systems, including clear mandates for resource backup, backup testing, restoration, auditing, and retention. Here is a summary of the exact DORA requirements related to these aspects, along with references to their respective clauses, I will then explain how to meet each of these requirements:
1. Backup Requirements
- Regular backups: Financial institutions must ensure regular backups of critical data and ICT resources. Backups should be done frequently and stored in secure locations.
Reference: Article 11, paragraph 1(b). - Data availability: Backup systems should ensure that critical data and systems remain available, even in cases of severe operational disruptions.
Reference: Article 11, paragraph 2.
2. Backup Testing
- Regular testing of backups: Backups should be tested periodically to ensure that the data can be recovered effectively. This includes testing for data integrity, recovery procedures, and accessibility of critical systems during potential incidents.
Reference: Article 11, paragraph 1(e). - Simulated disaster recovery: Financial entities must simulate disaster recovery scenarios to ensure that they can recover critical functions and data within the required timeframes.
Reference: Article 11, paragraph 4.
3. Restoration Requirements
- Timely restoration: Procedures for restoring critical data and ICT systems must be in place to ensure operational continuity within predefined recovery time objectives (RTOs).
Reference: Article 11, paragraph 1(d). - Recovery point objectives (RPOs): Institutions should set and maintain appropriate recovery point objectives to minimize data loss during recovery.
Reference: Article 11, paragraph 2(b).
4. Audit Requirements
- Audit trail: Financial institutions must maintain a comprehensive and secure audit trail of backup processes, testing procedures, and restoration activities to ensure traceability and accountability.
Reference: Article 16, paragraph 1. - Third-party audits: For outsourced backup or recovery services, financial entities must ensure that third-party providers also comply with audit requirements and that their performance is regularly reviewed.
Reference: Article 28, paragraph 4.
5. Retention Requirements
- Retention policies: Financial institutions must establish clear data retention policies for backup data, aligned with legal and regulatory obligations. These policies should ensure that data is retained for a period long enough to address operational and legal requirements, while also considering data minimization principles.
Reference: Article 11, paragraph 1(c). - Data deletion: Procedures must be in place to securely delete or dispose of backup data once the retention period has expired, in compliance with data protection laws (such as GDPR).
Reference: Article 11, paragraph 5.
6. Backup Security
- Access control: Backups must be protected by strong access control measures to prevent unauthorized access, alteration, or deletion. This includes encryption of backup data both in transit and at rest.
Reference: Article 11, paragraph 1(e). - Physical security: If backups are stored off-site or in a separate physical location, financial entities must ensure that these locations are secure and comply with applicable security requirements.
Reference: Article 11, paragraph 1(b).
7. Redundancy and Geographical Distribution
- Geographically diverse backup locations: Backups should be stored in geographically diverse locations to ensure that natural disasters or regional disruptions do not affect the ability to recover critical data.
Reference: Article 11, paragraph 1(b). - Redundant backup infrastructure: Institutions should maintain redundant backup systems to ensure continuous availability even if the primary backup system fails.
Reference: Article 11, paragraph 1(e).
8. Backup and Disaster Recovery Plan Integration
- Integration with disaster recovery plans: Backups must be integrated into the broader disaster recovery and business continuity plans. This includes ensuring backup procedures and recovery times align with overall incident response and resilience strategies.
Reference: Article 11, paragraph 1(d).
9. Outsourcing Backup Services
- Oversight of third-party providers: If backups are outsourced to third-party service providers (e.g., cloud providers), financial entities must ensure that the provider adheres to the same DORA requirements and regularly assess the provider’s performance, including backup reliability and security.
Reference: Article 28, paragraph 2.
10. Backup Documentation
- Documented backup processes: Institutions are required to document their backup strategies, including frequency, testing schedules, and recovery procedures. Documentation should be kept up to date and accessible to relevant personnel.
Reference: Article 11, paragraph 1(f).
11. Incident Notification
- Reporting backup failures: Any incident in which backup or recovery processes fail must be reported to the appropriate authorities as part of DORA’s incident reporting requirements.
Reference: Article 19, paragraph 1.
12. Continuous Monitoring and Improvement
- Continuous monitoring of backup systems: Financial entities must continuously monitor the effectiveness of their backup systems and adjust processes to address evolving risks or operational changes.
Reference: Article 12, paragraph 1.
First things first, I am assuming a few things that I will list down here:
- Multiple AWS accounts are running in a multi-account architecture
- All resources must be backed up
- You have control over all the resources that need to be backed up
- You know the data that is stored in the databases well and its legal retention requirement
Based on the requirements of DORA together with the assumption on how your infrastructure would look like, let’s draw a visual for better understanding:
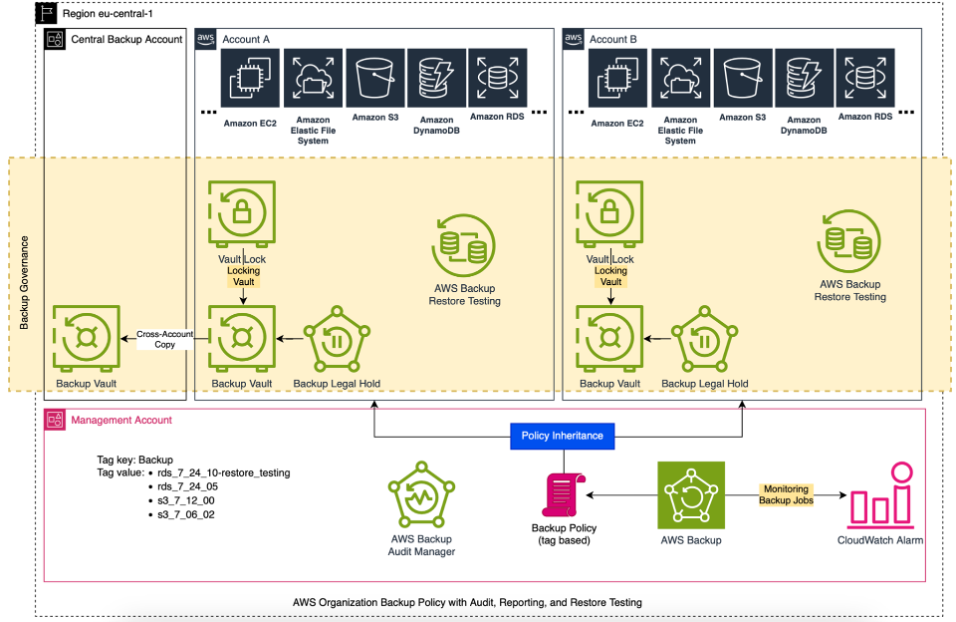
In the next parts I will explain how to implement each of the components that are in the diagram above and how to meet the DORA requirements.
End of Part 1 – Stay tuned!

Leave a Reply