In today’s digital world, ensuring your software is secure and trustworthy is more important than ever. With supply chain attacks becoming more common, code signing is one effective way to protect your software. In this article, I will walk you through what code signing is, why it’s essential, and how AWS Signer can help you do it at scale—while also keeping up with regulations like the EU’s DORA act.
What Is Code Signing?
Code signing is a process that ensures your software, like an app or script, hasn’t been changed or tampered with since the original author signed it. Essentially, it adds a digital signature to your code, which lets users or systems verify that the code is authentic and comes from a trusted source.
Code signing uses cryptographic techniques to embed a unique digital signature, which helps verify both the publisher’s identity and the software’s integrity. This means users can trust the code they’re running, protecting them from any malicious changes that could compromise security.
Why Should Code Be Signed?
Code signing is crucial for a few reasons:
- Security and Trust: The signed code shows that it comes from a legitimate source and hasn’t been altered since it was signed. This helps build user trust and reduces the chances of running compromised software.
- Protection Against Tampering: Unsigned code can be vulnerable to tampering by malicious actors. Code signing helps prevent this by providing a verification mechanism.
- Compliance: Many regulations and standards require software to be signed to ensure it follows best practices for security and compliance.
Code Signing Requirements in EU’s DORA Act
The Digital Operational Resilience Act (DORA) in the European Union sets strict requirements for financial institutions to secure their software supply chain. Under DORA, financial entities must ensure that their IT systems are secure, authentic, and trustworthy. Specifically, Article 15 of DORA requires that all critical software components be digitally signed to ensure integrity and authenticity. Code signing plays a key role here, as it helps organizations verify that the software they deploy hasn’t been altered and is from a trusted source.
Having a robust code-signing practice is crucial for companies aiming to meet these regulatory requirements and improve their cybersecurity posture. This is where AWS Signer comes in.
What Is AWS Signer?
AWS Signer is a fully managed code-signing service that helps you protect your software’s integrity by digitally signing it and ensuring it hasn’t been tampered with. With AWS Signer, security teams can define and manage the code-signing environment from one central place, making creating, maintaining, and auditing the signing process much more manageable.
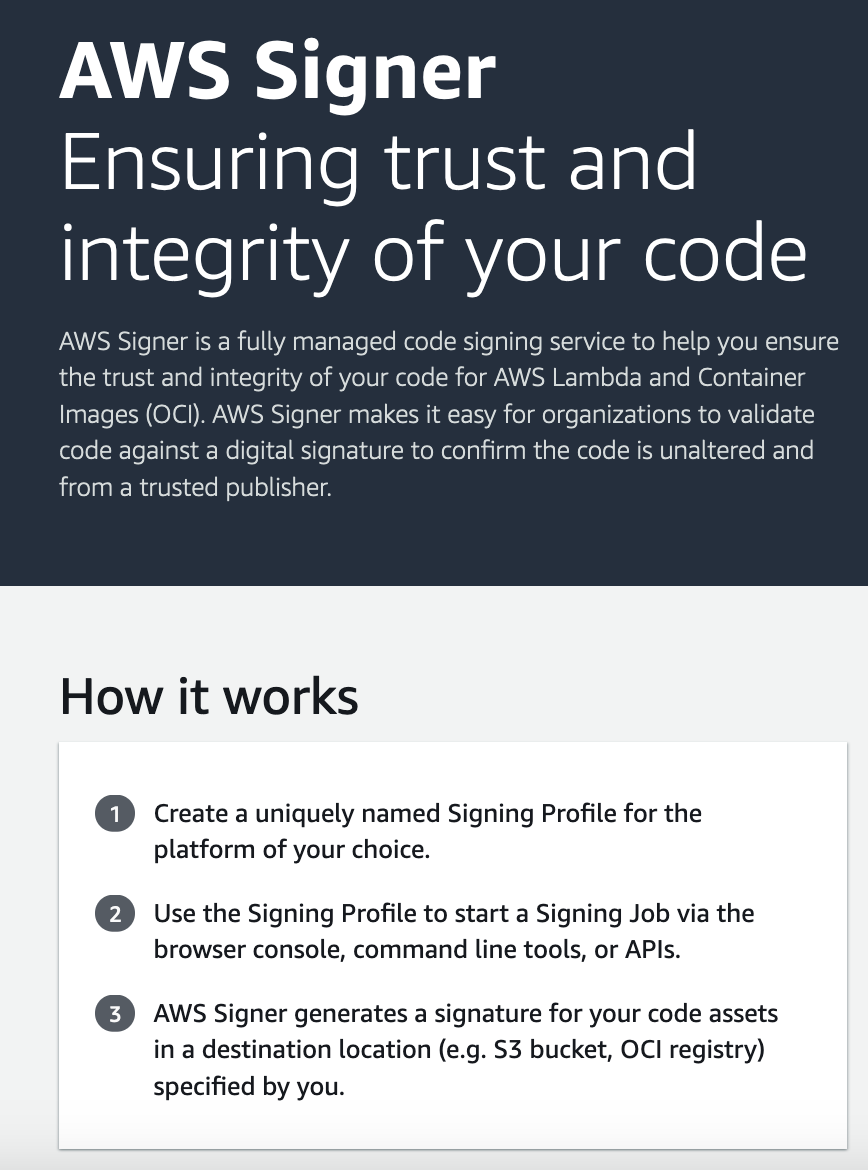
AWS Signer integrates with AWS Identity and Access Management (IAM) to handle permissions for signing and with AWS CloudTrail to track who generates signatures, which can help meet compliance needs. AWS Signer reduces the operational burden of manually handling certificates by managing both the public and private keys used in the code-signing process.
How to Use AWS Signer at Scale
Scaling code signing effectively can be challenging, especially for organizations with many applications and teams. AWS Signer has several features that make this easier:
- Centralized Key Management: AWS Signer works with AWS Key Management Service (KMS), allowing you to easily generate and manage signing keys securely.
- Automated Workflows: You can automate signing workflows using AWS Step Functions or integrate with CI/CD tools like AWS CodePipeline to make sure every build is signed before deployment.
- Compliance Tracking: With AWS CloudTrail integration, AWS Signer makes it simple to audit who signed what, which is key for regulatory compliance and internal governance.
For larger organizations, this centralized and scalable approach ensures that every piece of software across different teams and projects meets security and compliance standards. This is especially important for financial services companies that comply with regulations like DORA.
CI/CD Integration with AWS Signer
To maximize the benefits of code signing, integrating AWS Signer into your Continuous Integration and Continuous Deployment (CI/CD) pipeline is a great approach. This ensures that every code is signed automatically as part of your build and deployment processes, reducing manual effort and minimizing the risk of unsigned code slipping through. By integrating AWS Signer into your CI/CD pipeline, you can ensure that all your software releases are signed consistently and reliably.
CI/CD Integration with AWS Signer and Notary
To maximize the benefits of code signing, integrate AWS Signer into your Continuous Integration and Continuous Deployment (CI/CD) pipeline. This ensures that every piece of code is signed automatically as part of your build and deployment processes, reducing manual effort and minimizing the risk of unsigned code slipping through. If you use custom CI/CD solutions, you can leverage the AWS CLI or AWS SDK to interact with AWS Signer and add signing as part of your custom build or deployment scripts.
The Notary Project is an open-source initiative that aims to provide a platform-independent and secure way to sign, store, and verify software artifacts, such as container images. Originally developed by Docker, Notary aims to ensure the integrity and authenticity of distributed software by allowing users to establish trust through digital signatures.
In this article, I will be using Notary. Ensure that you have downloaded and installed Notary from here: https://notaryproject.dev/
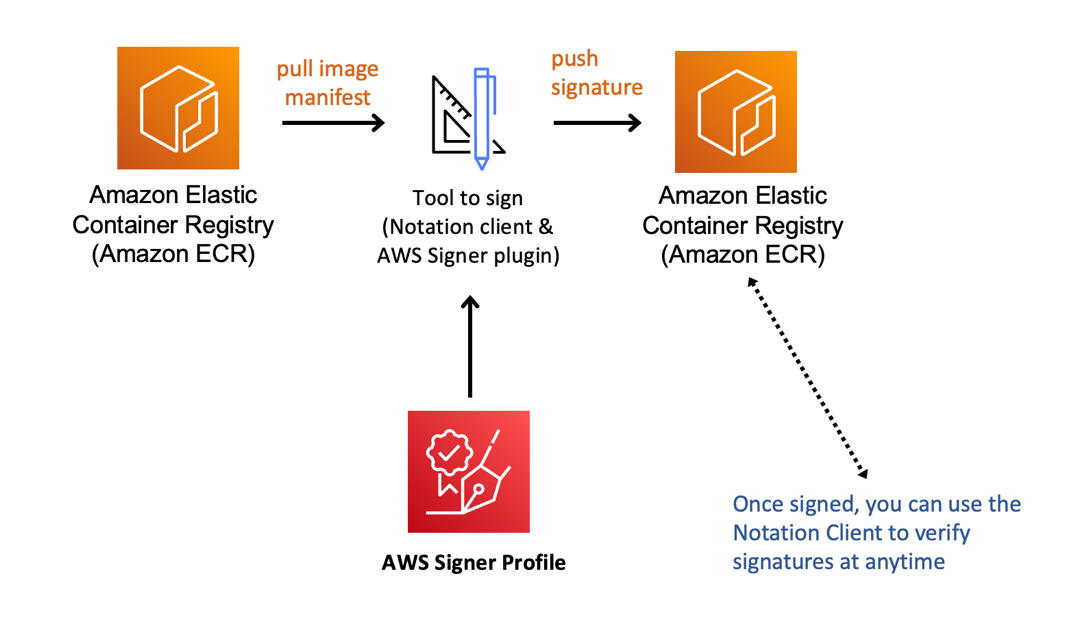
Before using the example below, you must ensure that a singer profile is created:
aws signer put-signing-profile --profile-name ecr_signing_profile --platform-id Notation-OCI-SHA384-ECDSAThen, authenticate:
aws ecr get-login-password --region Region | notation login --username AWS --password-stdin 111122223333.dkr.ecr.Region.amazonaws.comAnd finally, sign the image:
notation sign 111122223333.dkr.ecr.Region.amazonaws.com/curl@sha256:ca78e5f730f9a789ef8c63bb55275ac12dfb9e8099e6EXAMPLE --plugin "com.amazonaws.signer.notation.plugin" --id "arn:aws:signer:Region:111122223333:/signing-profiles/ecrSigningProfileName"Example: GitHub Actions Integration
To integrate AWS Signer with GitHub Actions, you can create a workflow that signs your code after building it. Here’s an example of how to do it:
name: Sign Code with AWS Signer
on:
push:
branches:
- main
jobs:
sign-code:
runs-on: ubuntu-latest
steps:
- name: Checkout code
uses: actions/checkout@v2
- name: Set up AWS CLI
uses: aws-actions/configure-aws-credentials@v2
with:
aws-access-key-id: \${{ secrets.AWS_ACCESS_KEY_ID }}
aws-secret-access-key: \${{ secrets.AWS_SECRET_ACCESS_KEY }}
aws-region: eu-central-1
- name: Build the code
run: |
# Add your build commands here
echo "Building code..."
- name: Sign the code with AWS Signer
run: |
aws signer start-signing-job \
--profile default \
--source "S3={"bucketName":"your-bucket","key":"your-code.zip"}" \
--profile-name "your-profile" \
--destination "S3={"bucketName":"signed-code","prefix":"signed/"}"In this example, the workflow checks out the code, sets up AWS credentials, builds the code, and then signs it using AWS Signer.
In a world where cyber threats are constantly growing, code signing isn’t just a best practice—it’s essential for keeping your software supply chain secure. A managed solution like AWS Signer can make code signing easier, help you meet regulatory requirements, and, most importantly, protect the organization and its customers from software supply chain attacks.
Ready to boost your software security? Start exploring AWS Signer today and make code signing a core part of your software development process.
Make sure to read this blog post on AWS before actually implementing the singer in your environment: https://aws.amazon.com/blogs/security/best-practices-to-help-secure-your-container-image-build-pipeline-by-using-aws-signer/
Reference:
- https://docs.aws.amazon.com/signer/latest/developerguide/Welcome.html
Stay tuned!
Leave a Reply